The Key to Efficient Access Control: Unleashing the Power of LDAP
In today’s digital world, organizations are entrusted with managing the identities and access permissions of countless users. Traditional methods, such as spreadsheets and local databases, are often inefficient, time-consuming, and prone to errors. This is where LDAP (Lightweight Directory Access Protocol) comes into play, offering a powerful and scalable solution for managing user identities and access control.
What is LDAP?
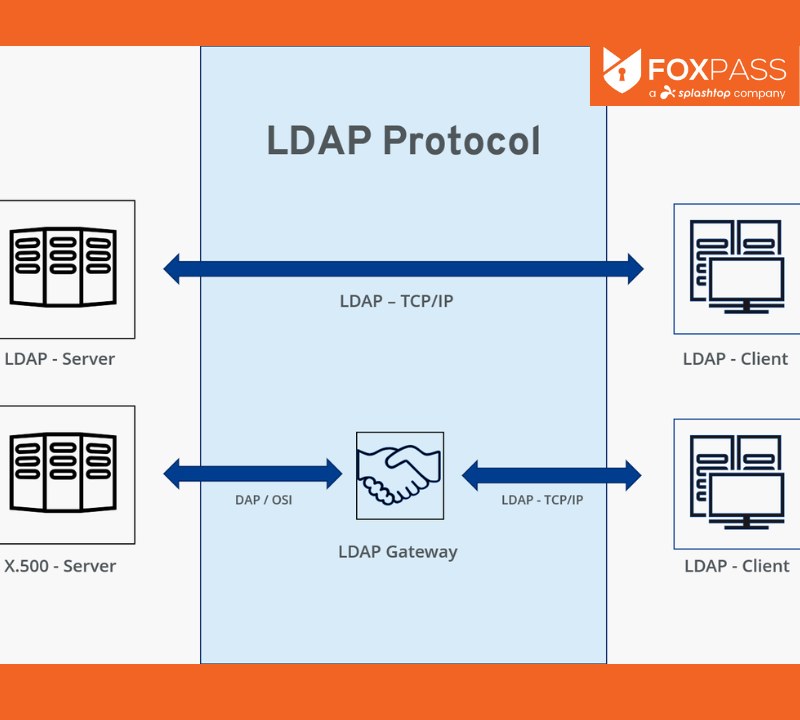
Opens in a new windowwww.researchgate.netLDAP server diagram
LDAP is an industry-standard protocol for storing and accessing directory information, such as user identities, groups, and organizational units. It acts as a central repository for user data, enabling administrators to manage access permissions and user information in a centralized and efficient manner.
Benefits of LDAP for Efficient Access Control:
- Centralized Management: Simplifies user management by storing all user data in a single location, eliminating the need for managing multiple databases or spreadsheets.
- Improved Security: Provides a robust security framework for user authentication and access control, reducing the risk of unauthorized access.
- Scalability: Designed to handle large numbers of users and groups, making it ideal for growing organizations.
- Flexibility: Integrates seamlessly with various applications and services, including email servers, network access control systems, and web applications.
- Enhanced User Experience: Enables single sign-on capabilities, allowing users to access multiple applications with a single set of credentials.
- Compliance: Helps organizations meet various regulatory requirements for data security and access control.
How Does LDAP Work?
The LDAP directory is organized in a hierarchical structure, similar to a file system. Each entry in the directory contains attributes, such as user name, email address, and group memberships. Clients interact with the LDAP server using search and modify operations to retrieve and update user information.
Here’s a breakdown of the process:
- Client: User attempts to access an application or resource.
- Application: Sends an LDAP query to the LDAP server requesting user information and access rights.
- LDAP Server: Searches the directory and retrieves the user’s information and access rights.
- Application: Grants or denies access based on the retrieved information and preconfigured access control policies.
Unleashing the Power of LDAP:
To fully realize the potential of LDAP, organizations need to:
- Implement a Robust Directory Structure: Design a well-structured directory with clear organizational units and attribute definitions.
- Define Access Control Policies: Clearly define access rights for different groups and users to ensure appropriate access levels.
- Integrate with Applications and Services: Integrate LDAP with other systems to leverage user information for various purposes.
- Implement Security Best Practices: Regularly update LDAP software, enforce strong passwords, and monitor directory activity for anomalies.
The Future of LDAP:
In the ever-evolving digital landscape, LDAP continues to be a crucial tool for efficient access control. With the growing emphasis on cloud computing and mobile access, organizations can benefit from the scalability and flexibility of LDAP to manage user identities and access permissions effectively.
Looking ahead, we can expect to see:
- Greater Integration with Cloud Services: LDAP integration with cloud platforms will enable seamless user management across cloud applications.
- Enhanced Security Features: LDAP implementations will incorporate advanced security features, such as multi-factor authentication and biometrics, to further strengthen access control.
- Improved User Experience: Developments will focus on user-centric features, such as self-service password resets and single sign-on across diverse platforms.
Conclusion:
By embracing LDAP, organizations can unlock the power of efficient access control, improve user experience, and enhance security. With its scalability, flexibility, and robust security features, LDAP remains a vital tool for organizations of all sizes to manage user identities and ensure secure access to valuable resources.